The Triangle wave as coming out of the function generator
The square wave as coming out of the function generator
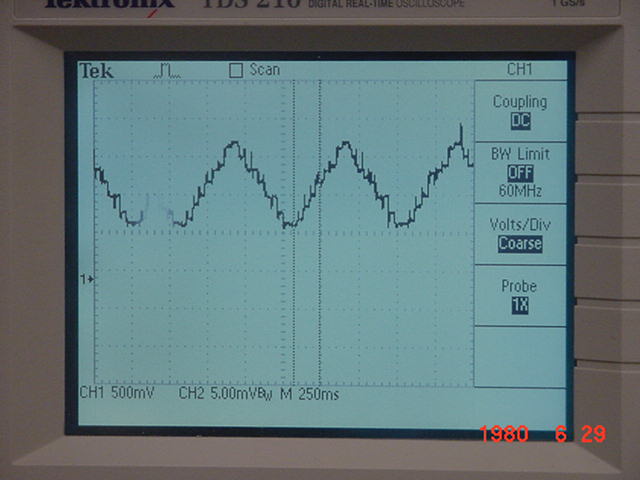
The Triangle wave as coming out of the DAC
The Square Wave as coming out of the DAC
The Triangle wave as coming out of the function generator |
The square wave as coming out of the function generator |
 The Triangle wave as coming out of the DAC |
The Square Wave as coming out of the DAC |
| Jonathan · Xilinx schematic · Failed hardware construction · Interrupt service routines · General ASM and C debugging and reworking · Algorithmic research |
Victor · RSA research · C coding · ASM timer set up |